Initialize BitLocker
Description
This script serves as the enforcement engine that automatically corrects BitLocker configuration issues identified by the detection logic. Designed as a wrapper for an agnostic encryption solution, it first prepares the environment by ensuring the correct security protocols (TLS 1.2/1.3) are active and establishing a secure working directory. It then parses the same custom fields to understand the required policy. Based on the current state of the drive, the script performs intelligent remediation actions: it will inject a missing Recovery Password without decrypting, or fully disable and re-encrypt the drive if the encryption algorithm or key protector type is incorrect. If decryption is required, the script enters a monitored wait loop to ensure the drive is fully clean before re-attempting encryption. Finally, it executes the core encryption logic to apply the correct settings, ensuring the device becomes fully compliant without requiring manual administrator intervention.
Crucially, this script performs a mandatory post-execution audit regardless of the initialization outcome (success or failure). It captures the current BitLocker state—including active Recovery Passwords—and writes them immediately to NinjaOne Custom Fields. This acts as a safety net, ensuring that recovery keys are stored in the RMM immediately. This is vital for devices without TPMs (using RecoveryPassword protectors), where a drive might lock before keys have time to sync to Active Directory or Azure AD, preventing potential data loss.
Note:
- This is only compatible for Windows devices.
- If no mount point is provided in the Custom field, it will encrypt "C" Drive by default.
- The BitLocker Drive Encryption feature must be enabled on servers to encrypt a drive with BitLocker disk encryption. Encryption will not work without enabling this feature.
Requirements
- PowerShell v5
- Update the custom fields with the data so that script will use that settings.
Sample Run
Dependencies
- Custom Field - cPVAL Allow TPM Or Reboot
- Custom Field - cPVAL SkipHardwareTest
- Custom Field - cPVAL EncryptionMethod
- Custom Field - cPVAL KeyProtectorType
- Custom Field - cPVAL Mountpoint
- Custom Field - cPVAL Path Or ADAccount
- Custom Field - cPVAL PIN Or Password
- Custom Field - cPVAL BitLocker Enabled for System Drive
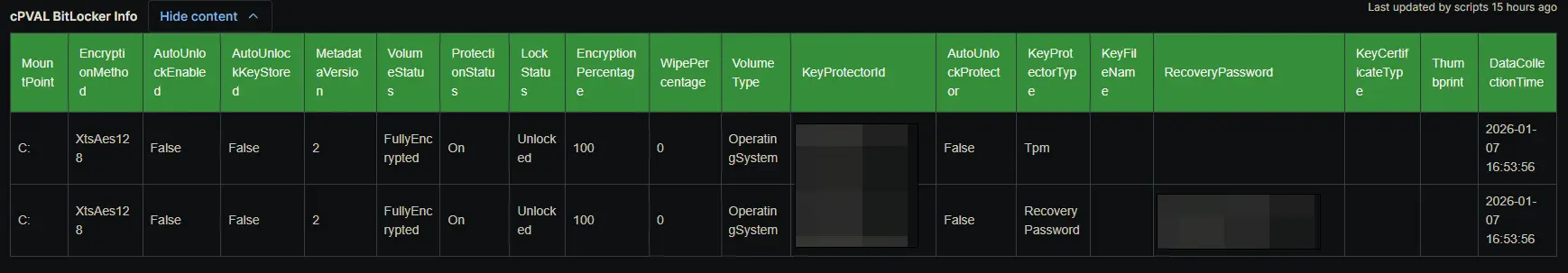
- Custom Field - cPVAL BitLocker Info
- Agnostic - Initialize-BitLockerVolume
- Solution - BitLocker Initialize - NinjaOne
Custom Fields
| Field Label | Scope | Accepted Values | Default Value | Description |
|---|---|---|---|---|
| cPVAL MountPoint | Organization, Location, Device | Drive Letter (e.g., C: or D:) | $env:SystemDrive | The drive letter to initialize BitLocker on. |
| cPVAL EncryptionMethod | Organization, Location, Device | XTSAES128, XTSAES256, AES128, AES256 | XtsAes128 | The encryption algorithm to apply. |
| cPVAL KeyProtectorType | Organization, Location, Device | TPM, TpmPin, TpmStartup, TpmPinStartup, Password, Startup, RecoveryKey, RecoveryPassword, AdAccount | RecoveryPassword | The primary authentication method used to unlock the drive. |
| cPVAL PIN Or Password | Organization, Location, Device | String (Any valid PIN or Password) | $null | Required if TpmPin or Password is selected. |
| cPVAL Path Or ADAccount | Organization, Location, Device | String (UNC Path, Drive Path, or AD User/Group) | $null | Required for Startup, RecoveryKey, or AdAccount. |
| cPVAL Allow TPM Or Reboot | Organization, Location, Device | 0 = None1 = Allow TPM Init2 = Allow Restart3 = Allow Both | 0 | Controls if the script can initialize TPM or reboot the machine. |
| cPVAL SkipHardwareTest | Organization, Location, Device | $false | Skips the hardware pre-check (faster, but riskier). | |
| cPVAL BitLocker Info | Device | Stores the HTML-formatted inventory of BitLocker volumes and protectors. | ||
| cPVAL BitLocker Enabled for System Drive | Device | indicating if the Operating System drive is encrypted. |
Automation Setup/Import
Output
- Activity Logs
- Custom Fields
cPVAL BitLocker Info
cPVAL BitLocker Enabled for System Drive