SMBv1AuditAutofix
Purpose
This solution contains the SMBv1 audit and autofix based on the EDF.
Associated Content
| Content | Type | Function |
|---|---|---|
| Script - SMBv1 Status Audit/Autofix [DV,Param] | Script | This script is created to run the detection/remediation for SMBv1 Enabled based on EDF. It will act only if the dropdown EDF "SMB1 Vulnerability" is set to 'Audit Only' or 'Audit With Autofix' at any client, location, or computer level. |
| Script - SMBv1 Enable Detection Ticketing - Per Client | Client Script | This client script creates a ticket for each client with the computer count where remediation is required. |
| Script - SMB1 Traffic Detection Monitor Creation | Client Script | Remote monitors "ProVal - Production - SMB1 Traffic Detection" will be set up on computers where the SMB1 Detection remote monitor identifies the SMB1 Server Status as Enabled. In the Dataview - SMBv1 Status Audit, the SMB1 Server Status column will display Enabled for these machines. Dataview - SMBv1 Status Audit gathers the state of the monitor failure to show the machines where the SMB1 is used. |
| Dataview - SMBv1 Status Audit | Dataview | This dataview gathers the data from the script CWA Script - SMBv1 Enabled Detection & Remediation and depicts the status of SMB Enabled on the agent where it is deployed. |
| Remote Monitor - SMB1 Detection | Remote Monitor | Checks whether SMB1 is enabled on the end machine. It runs the OS version compatible command to fetch the data. |
| Internal Monitor - SMB1 Autofix | Internal Monitor | This internal monitor detects online Windows agents and performs autofix on computers where the "Audit with Autofix" is set via client, location, or computer level EDF "SMB1 Vulnerability". The Remote Monitor - SMB1 Detection shows failure, and the autofix Script - SMBv1 Status Audit/Autofix [DV, Param] has not run in the past week. |
| △ Custom - Execute Script - SMB1 Audit/Autofix | Alert Template | This needs to be scheduled with the Remote Monitor - SMB1 Detection and the Internal Monitor - SMB1 Autofix to perform the Audit and Autofix based on EDF selection at the client, location, or computer level. |
Implementation
Remove Old Solution
If this solution is approved, please remove the following DV and Remote monitor:
- EPM - Windows Configuration - Dataview - SMB1 Status [Remote Monitor]
- EPM - Windows Configuration - Remote Monitor - SMB1 Detection
To remove them, please run the following query:
DELETE FROM groupagents WHERE NAME = 'ProVal - Production - SMB1 Detection';
DELETE FROM agents WHERE NAME = 'ProVal - Production - SMB1 Detection' AND computerid > 0;
DELETE FROM dataviews WHERE name = 'SMB1 Status [Remote Monitor]';
Import New Solution
-
Import the following content using the ProSync Plugin:
- Script - SMBv1 Status Audit/Autofix [DV,Param]
- Script - SMBv1 Enable Detection Ticketing - Per Client
- Script - SMB1 Traffic Detection Monitor Creation
- Dataview - SMBv1 Status Audit
- Internal Monitor - SMB1 Autofix
- Alert Template -
△ Custom - Execute Script - SMB1 Audit/Autofix
Import the EDFs, Searches, Groups, and Remote monitor following the document below:
- Import - Remote Monitor - SMB1 Detection Query
-
Reload the system cache:
-
Configure the solution as outlined below:
- Navigate to Browse → Groups (△ System Monitoring→△ Vulnerability Management) → Computers→ Remote monitors within the CWA Control Center and set the following:
- Remote Monitor - SMB1 Detection
- Validate that the monitor is configured with the alert template "
Default - Do Nothing" and if it is not, assign the alert template manually to perform the status audit and autofix based on the EDF selection.
- Validate that the monitor is configured with the alert template "
- Remote Monitor - SMB1 Detection
- Navigate to Automation → Monitors within the CWA Control Center and set up the following:
- Internal Monitor - SMB1 Autofix
- Set up with
△ Custom - Execute Script - SMB1 Audit/AutofixAlert Template - Right-click and Run Now to start the monitor
- Set up with
- Internal Monitor - SMB1 Autofix
- Schedule the client script "Script - SMB1 Traffic Detection Monitor Creation" to gather the SMB1 live used state from the machines based on the event ID detection.
- This client script will deploy the remote monitor to all the computers where "Remote Monitor - SMB1 Detection" has detected SMB1 enabled.
- The Dataview - SMBv1 Status Audit gathers the state of the monitor "ProVal - Production - SMB1 Traffic Detection" and shows data as "Yes" or "No" if used or not used, respectively.
Note: Group "△ Vulnerability Management" under "△ System Monitoring" is created as a standard group to maintain a record of all monitors being developed in the future to be applied from it.

It contains all Windows Servers and Workstations whose onboarding is completed and service plans are under contract.
Therefore, it is mandatory to validate that the monitors applied to this group have their Limit applied based on the Audit or Audit with Autofix selection; otherwise, it will be applied to all Windows machines. - Navigate to Browse → Groups (△ System Monitoring→△ Vulnerability Management) → Computers→ Remote monitors within the CWA Control Center and set the following:
-
NOTE: WE SHOULD ONLY BE PERFORMING THESE STEPS IF ASKED BY THE CONSULTANT
To enable the solution, please make sure to select any one Audit option from the drop-down EDFs "SMB1 Vulnerability" at the computer, location, or client level. The 'Additional Field Default' value can also be selected here to enable the solution globally.
- Audit with Autofix → If this is selected, then SMB1 will be automatically disabled if found enabled on any device.
- Both the SMB1 client and SMB1 server will be disabled.
- Audit Only → If this is selected, then the SMB1 status will be audited only and will not be automatically disabled if found to be enabled.
Note: The computer-level EDF "SMB1 Vulnerability" has the highest priority; if it is set to disabled, then it will be excluded. The location-level EDF "SMB1 Vulnerability" has the second-highest priority; if it is set to disabled, then all the endpoints at the location level will be excluded.
- Audit with Autofix → If this is selected, then SMB1 will be automatically disabled if found enabled on any device.
Optional Solutions
Traffic Detection Ticketing
Optionally, if the client wants, we can enable ticketing to monitor the SMB1 traffic live detection cases separately for each machine by setting up the system properties:
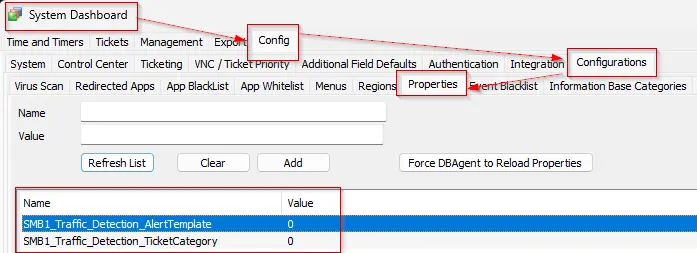
Note: This should only be implemented if the consultant approves it.