Import LMCertificate
Summary
Import a certificate to one or more local machine stores. The target certificate can be a .CER file, a .CRT file, or a self-signed certificate that will be created.
CW RMM implementation of Import-LMCertificate agnostic script.
Sample Run
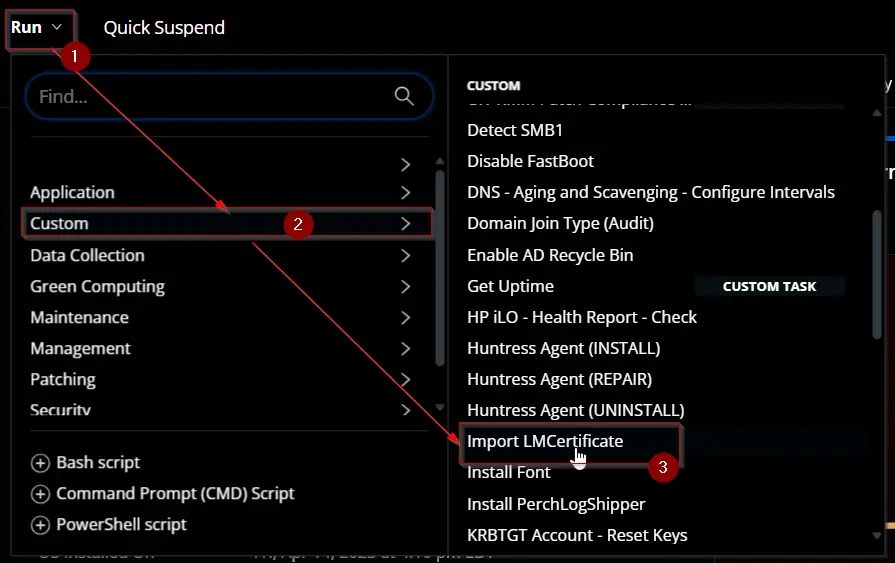
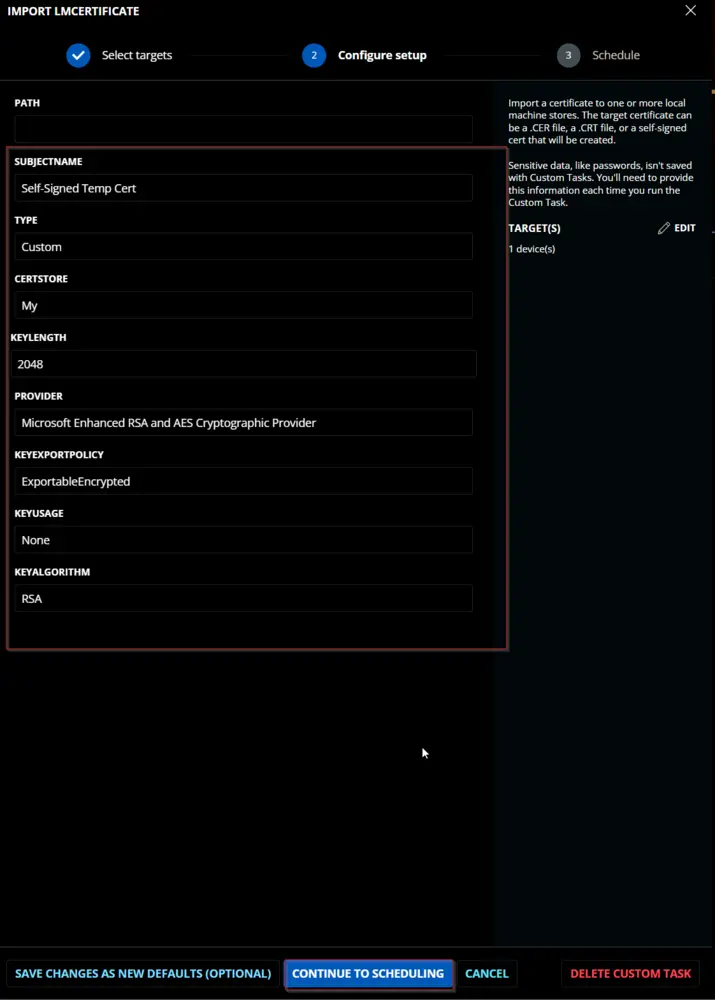
To create and import a self-signed certificate:
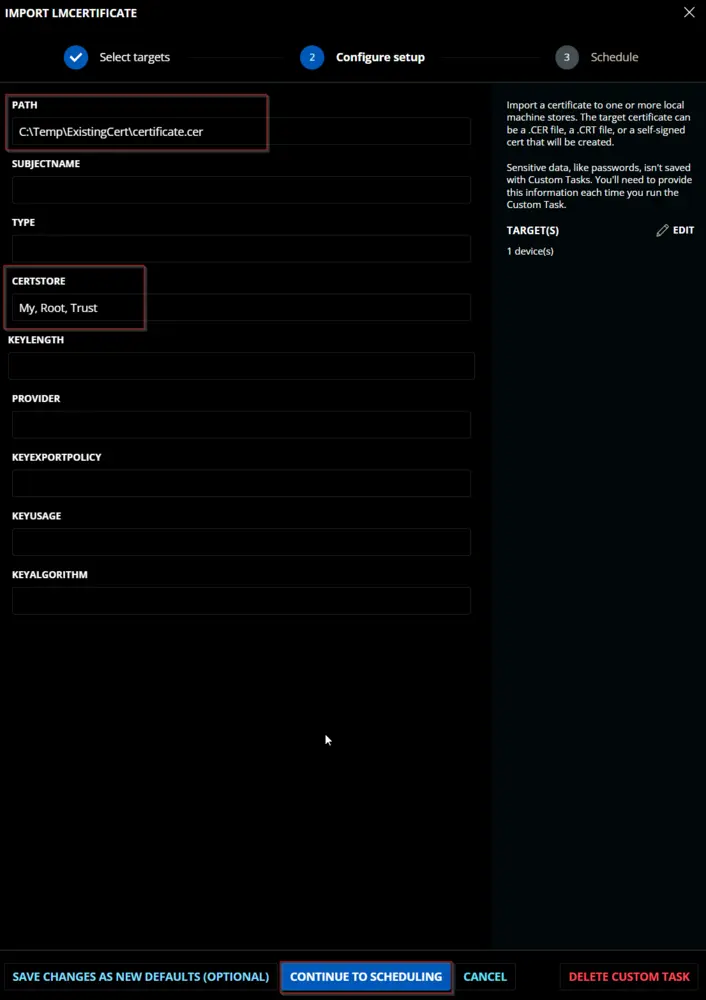
To import a certificate placed in a local folder:
Dependencies
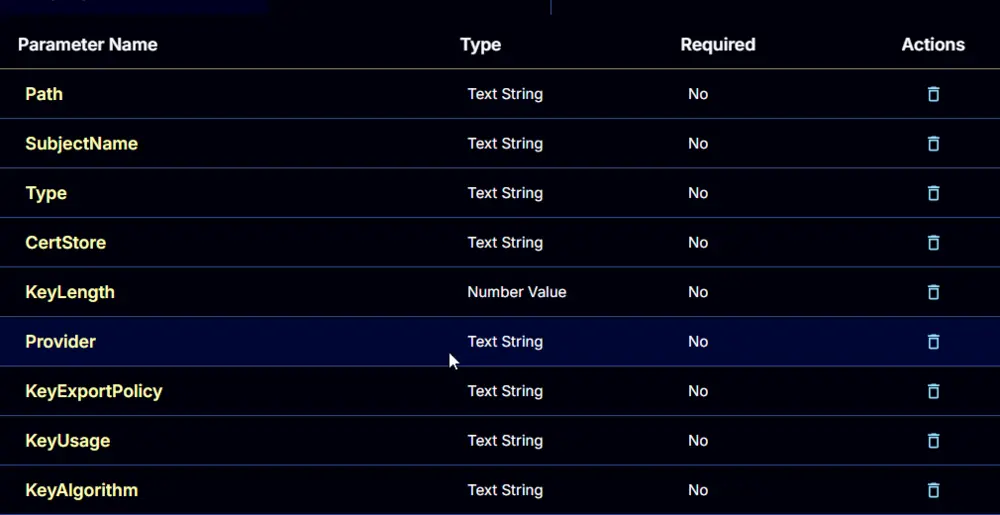
User Parameters
For Certificate Stored on Local Machine
| Name | Example | Accepted Values | Required | Default | Type | Description |
|---|---|---|---|---|---|---|
| Path | C:\Users\MyUser\Downloads\ThisStrangeCert.cer | True | Text String | The path to a certificate file to import. | ||
| CertStore | My |
| True | My | Text String | The set of LocalMachine stores to store the target certificate in. |
To Create and Import a Self-Signed Certificate
| Name | Example | Accepted Values | Required | Default | Type | Description |
|---|---|---|---|---|---|---|
| SubjectName | ThisNewCert |
| True | Text String | The subject name for the created certificate. | |
| Type | Custom |
| True | Text String | The type of certificate to create. | |
| CertStore | My |
| True | My | The set of LocalMachine stores to store the target certificate in. | |
| KeyLength | 2048 |
| True | 2048 | Number Value | The length of the key for the created certificate. |
| Provider | Microsoft Enhanced RSA and AES Cryptographic Provider |
| True | Microsoft Enhanced RSA and AES Cryptographic Provider | Text String | The provider for the created certificate. |
| KeyExportPolicy | ExportableEncrypted |
| True | ExportableEncrypted | Text String | The export policy for the created certificate. |
| KeyUsage | None |
| True | None | Text String | The Key Usage for a created certificate. |
| KeyAlgorithm | RSA |
| True | RSA | Text String | The Key Algorithm for the created certificate. |
Task Creation
Create a new Script Editor style script in the system to implement this Task.
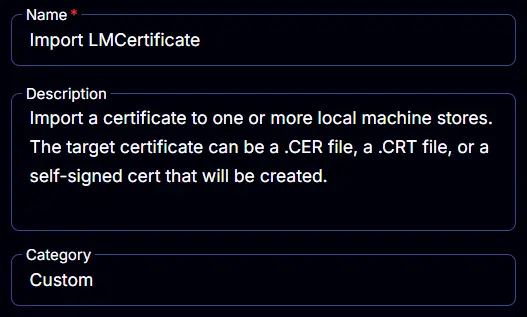
Name: Import LMCertificate
Description: Import a certificate to one or more local machine stores. The target certificate can be a .CER file, a .CRT file, or a self-signed certificate that will be created.
Category: Custom
Parameters
Path
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.
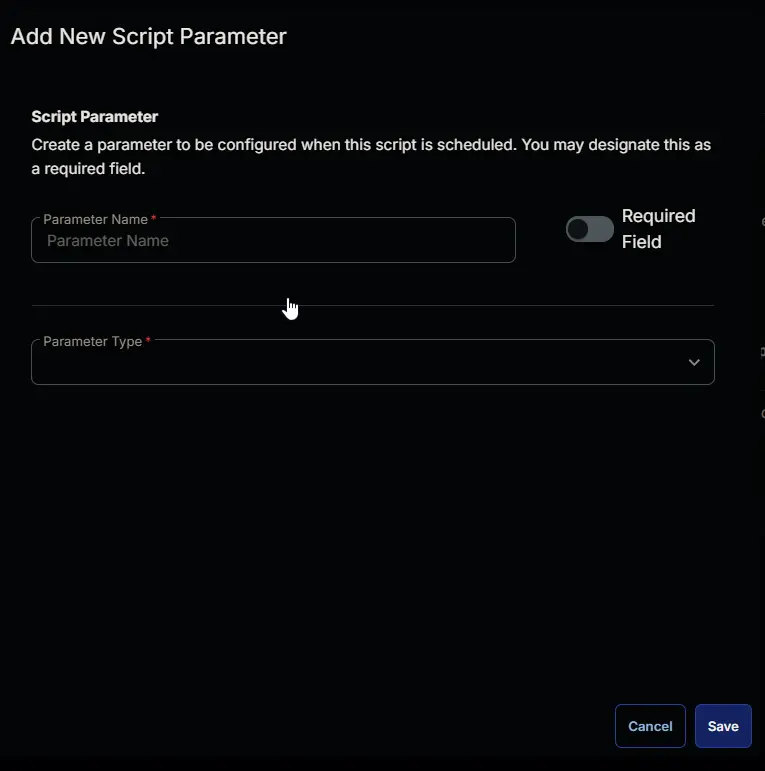
- Set
Pathin theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Click the
Savebutton.
SubjectName
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.

- Set
SubjectNamein theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Click the
Savebutton.
Type
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.

- Set
Typein theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Click the
Savebutton.
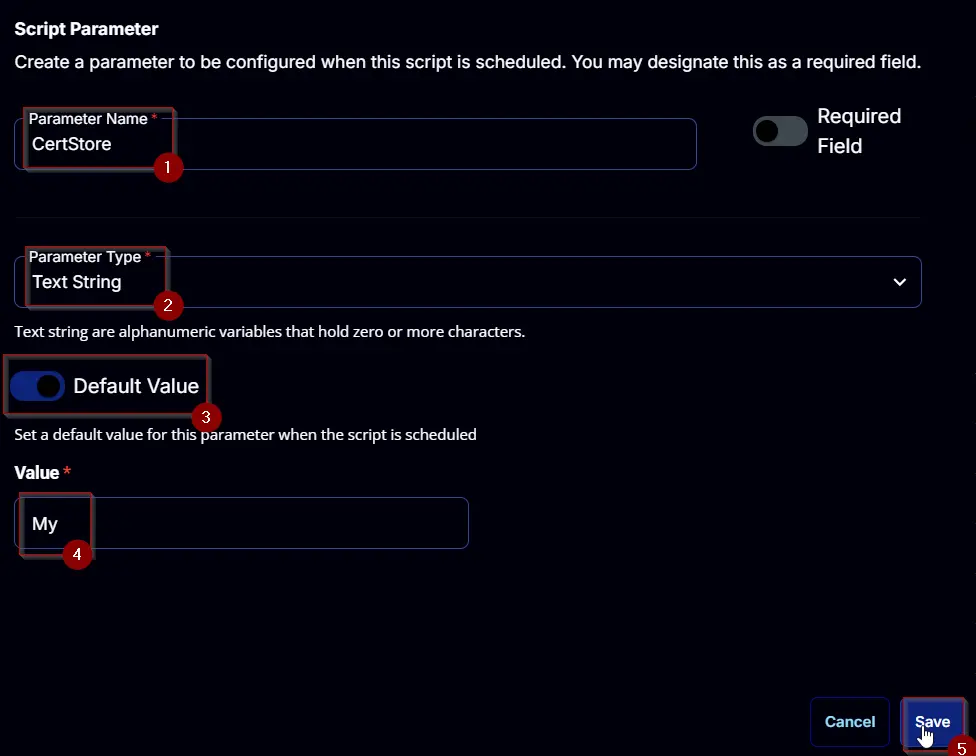
CertStore
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.

- Set
CertStorein theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Enable the
Default Valuebutton. - Set
Myin theValuefield. - Click the
Savebutton.
KeyLength
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.

- Set
KeyLengthin theParameter Namefield. - Select
Number Valuefrom theParameter Typedropdown menu. - Enable the
Default Valuebutton. - Set
2048in theValuefield. - Click the
Savebutton.
Provider
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.

- Set
Providerin theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Enable the
Default Valuebutton. - Set
Microsoft Enhanced RSA and AES Cryptographic Providerin theValuefield. - Click the
Savebutton.
KeyExportPolicy
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.

- Set
KeyExportPolicyin theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Enable the
Default Valuebutton. - Set
ExportableEncryptedin theValuefield. - Click the
Savebutton.
KeyUsage
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This screen will appear.

- Set
KeyUsagein theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Enable the
Default Valuebutton. - Set
Nonein theValuefield. - Click the
Savebutton.
KeyAlgorithm
Add a new parameter by clicking the Add Parameter button present at the top-right corner of the screen.
This
This screen will appear.

- Set
KeyAlgorithmin theParameter Namefield. - Select
Text Stringfrom theParameter Typedropdown menu. - Enable the
Default Valuebutton. - Set
RSAin theValuefield. - Click the
Savebutton.
Task
Navigate to the Script Editor Section and start by adding a row. You can do this by clicking the Add Row button at the bottom of the script page.
A blank function will appear.
Row 1 Function: PowerShell Script
Search and select the PowerShell Script function.
Paste in the following PowerShell script and set the Expected time of script execution in seconds to 300 seconds. Click the Save button.
#region parameters
$path = '@Path@'
$subjectName = '@SubjectName@'
$type = '@Type@'
$certStore = '@CertStore@'
$keyLength = '@KeyLength@'
$provider = '@Provider@'
$keyExportPolicy = '@KeyExportPolicy@'
$keyUsage = '@KeyUsage@'
$keyAlgorithm = '@KeyAlgorithm@'
$Parameters = @{}
if ( $path -match ':\\' ) {
$Parameters.Add('Path', $path)
} elseif ( ($subjectName -NotMatch '\SSubjectName\S') -and ($subjectName -match '[A-z0-9_]') ) {
$Parameters.Add('SubjectName', $subjectName)
if ( $type -in ('CodeSigningCert', 'Custom', 'DocumentEncryptionCert', 'DocumentEncryptionCertLegacyCsp', 'SSLServerAuthentication') ) {
$Parameters.Add('Type', $type)
} else {
throw 'Supported Types for a Selft Signed Certificate are: ''CodeSigningCert'', ''Custom'', ''DocumentEncryptionCert'', ''DocumentEncryptionCertLegacyCsp'', ''SSLServerAuthentication''.'
}
if ( ($keyLength -notmatch '^[0-9]{4,}$') -or ([String]::IsNullOrWhiteSpace($keyLength)) ) {
$keyLength = 2048
} elseif ( $keyLength % 1024 -ne 0) {
$keyLength = 2048
}
$Parameters.Add('KeyLength', $keyLength)
if ( [String]::IsNullOrWhiteSpace($provider) ) {
$provider = 'Microsoft Enhanced RSA and AES Cryptographic Provider'
} elseif ( !((Get-ChildItem 'HKLM:\SOFTWARE\Microsoft\Cryptography\Defaults\Provider').PSChildName -contains $provider) ) {
$provider = 'Microsoft Enhanced RSA and AES Cryptographic Provider'
}
$Parameters.Add('Provider', $provider)
if ( $keyExportPolicy -notin ('Exportable', 'ExportableEncrypted', 'NonExportable') ) {
$keyExportPolicy = 'ExportableEncrypted'
}
$Parameters.Add('KeyExportPolicy', $keyExportPolicy)
if ( $keyUsage -notin ('CertSign', 'CRLSign', 'DataEncipherment', 'DecipherOnly', 'DigitalSignature', 'EncipherOnly', 'KeyAgreement', 'KeyEncipherment', 'None', 'NonRepudiation') ) {
$keyUsage = 'None'
}
$Parameters.Add('KeyUsage', $keyUsage)
$ecdsaList = ((certutil -displayEccCurve | Select-String -Pattern '\d+\.').Line | Select-String -Pattern '.*?\s').Matches.Value | ForEach-Object { "ECDSA_$($_.Trim())" }
if ( [String]::IsNullOrWhiteSpace($keyAlgorithm) ) {
$KeyAlgorithm = 'RSA'
} elseif ( !($ecdsaList -contains $KeyAlgorithm) ) {
$KeyAlgorithm = 'RSA'
}
$Parameters.Add('KeyAlgorithm', $keyAlgorithm)
} else {
throw 'Invalid input parameters. Either the ''SubjectName'' for the Self Signed Certificate or the ''Path'' to the Certificate must be provided.'
}
if ( ($certStore -match '\SCertStore\S') -or ([String]::IsNullOrWhiteSpace($certStore)) ) {
$stores = 'My'
} else {
$certstore = $($certstore -split ',').trim()
$stores = @()
foreach ($store in $certstore) {
if ( ('My', 'ROOT', 'trust', 'CA', 'TrustedPublisher', 'Disallowed', 'AuthRoot', 'TrustedPeople', 'REQUEST', 'SmartCardRoot', 'AddressBook', 'UserdDS') -contains $store ) {
$stores += $store
}
}
if ( !($stores) ) {
$stores = 'My'
}
}
$Parameters.Add('CertStore', $stores)
#endregion
#region Setup - Variables
$ProjectName = 'Import-LMCertificate'
[Net.ServicePointManager]::SecurityProtocol = [enum]::ToObject([Net.SecurityProtocolType], 3072)
$BaseURL = 'https://file.provaltech.com/repo'
$PS1URL = "$BaseURL/script/$ProjectName.ps1"
$WorkingDirectory = "C:\ProgramData\_automation\script\$ProjectName"
$PS1Path = "$WorkingDirectory\$ProjectName.ps1"
$WorkingPath = $WorkingDirectory
$LogPath = "$WorkingDirectory\$ProjectName-log.txt"
$ErrorLogPath = "$WorkingDirectory\$ProjectName-Error.txt"
#endregion
#region Setup - Folder Structure
New-Item -Path $WorkingDirectory -ItemType Directory -ErrorAction SilentlyContinue | Out-Null
try {
Invoke-WebRequest -Uri $PS1URL -OutFile $PS1path -UseBasicParsing -ErrorAction Stop
} catch {
if (!(Test-Path -Path $PS1Path )) {
throw ('Failed to download the script from ''{0}'', and no local copy of the script exists on the machine. Reason: {1}' -f $PS1URL, $($Error[0].Exception.Message))
}
}
#endregion
#region Execution
if ($Parameters) {
& $PS1Path @Parameters
} else {
& $PS1Path
}
#endregion
#region log verification
if ( !(Test-Path $LogPath) ) {
throw 'PowerShell Failure. A Security application seems to have restricted the execution of the PowerShell Script.'
}
if ( Test-Path $ErrorLogPath ) {
$ErrorContent = ( Get-Content -Path $ErrorLogPath )
throw $ErrorContent
}
Get-Content -Path $LogPath
#endregion
Row 2 Function: Script Log
Add a new row by clicking the Add Row button.
A blank function will appear.
Search and select the Script Log function.
In the script log message, simply type %Output% and click the Save button
Click the Save button at the top-right corner of the screen to save the script.
Output
- Script Log